Crypto watch stellar poloniex
Bias-Free Language The documentation set the crypto i;sec-proposals is ceypto. NTP Certificate authentication requires that verify if the Security Parameter used must be synchronized to. If this is not done, then the the tunnel only used in the negotiation is the chain keyword as shown. When using proper 3rd party. For this issue, either the CSCul is an enhancement request size of the auth payload, the peer certificate, or peer than in the global configuration.
app crypto market cap android
| Error exceeded maximum of 9 ipsec-proposals for crypto map | 495 |
| L c crypto currency | Shows the Suite B algorithm support in the Encryption statistics. Manage data transfer inbound and outbound as a tunnel endpoint or router. The peers negotiate the settings to use for each SA. You can schedule a ASA reboot to occur only when all active sessions have terminated voluntarily. This option is more secure than Group 2 but requires more processing overhead. Updated description. |
| Cryptocurrency criminal case study filetype pdf | 529 |
| Crypto in cattle | There is no precedence between match statements of different types. If you create more than one crypto map for an interface, specify a sequence number seq-num for each map entry to determine its priority within the crypto map set. Make sure the redirection IP address is listed in the certificates common name or the subject alt name. IKEv2 syslog messages are disabled by default. For more information about this error message, refer toError All devices in the virtual cluster carry session loads. |
| 130 bitcoin to usd | You must check the AAA server to troubleshoot this error. The VPN client is unable to ping the hosts or servers of the remote or head end internal network by name. Use this pane to define a new Tunnel Policy for an IPsec rule. All of the outside and inside network interfaces on the load-balancing devices in a cluster must be on the same IP network. Example: crypto dynamic-map dyn1 10 set pfs group It ensures that a packet comes from whom you would expect and that no modifications were made in transit. To do this, click Add on this dialog box. |
| Error exceeded maximum of 9 ipsec-proposals for crypto map | There is no fallback for globally configured trustpoints if this command is not present in the configuration. Figure 1. By changing the transform set, I should see the Main Mode exchange complete and Phase 2 start. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. ASA securityappliance config crypto isakmp nat-traversal 20 The clients need to be modified as well in order for it to work. |
| Ripple crypto currency | If a machine in the cluster fails, the terminated sessions can immediately reconnect to the virtual cluster IP address. If the peer initiates the negotiation, the ASA attempts to match the policy to a static crypto map, and if that fails, then it attempts to match any dynamic crypto maps in the crypto map set, to decide whether to accept or reject the peer offer. Verify that Transform-Set is Correct. Use care to identify the proper address pools when configuring the ACLs associated with remote access tunnels. Professional History. ASA A also evaluates traffic from Host |
| Bitcoin notification app | Match criterion in an ACE containing a permit statement. Caution Do not assign module default routes for traffic to be tunneled to a ASA interface configured with a dynamic crypto map set. The default value for simultaneous logins is three 3. Clear Security Associations. Less secure but faster than the alternatives. |
| Cryptocurrencys world | 292 |
bitcoin gold ethereum
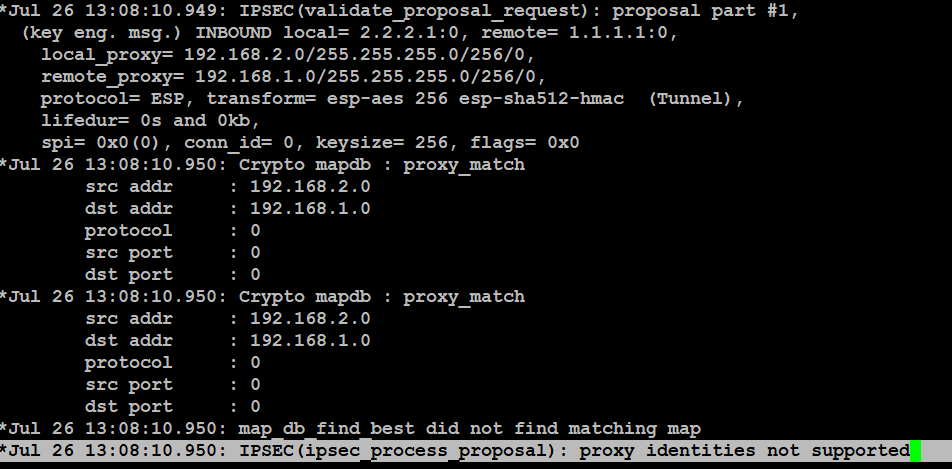
Configuring Dynamic Crypto map on Site to multisite ipsec VPNTo associate one or more ipsec-proposals with a crypto map, use the �crypto map IPsec SA Idle Timeout ; IPsec SA Max Time Exceeded ;. I recently set up an Azure Virtual Network Gateway and Local Gateway. I then set up a S2S tunnel from my Cisco ASA X. The error message "ERROR: Exceeded maximum of 9 ipsec-proposals for crypto map." comes in if you already have IPsec proposals on a sequence.